Introduction to Managing Third Party Risk
With the increasing frequency and sophistication of cyber-attacks, businesses worldwide must be vigilant about securing their systems, networks, and information. One crucial aspect of cybersecurity that often gets overlooked is third-party risk. In this blog post, we will explore why third-party risk management (TPRM) is essential, how to implement it, and what to consider when assessing third-party suppliers.
The Rising Cost of Data Breaches
Most businesses procure services from third-party vendors or suppliers, which can pose financial, reputational, compliance, legal, and other risks.
Globally, just under 30% of organisations are likely to suffer at least one breach over the next 24 months. The average data breach now involves 34,249 data records, costing an average of $141 per compromised record.Data breaches, which often originate from vendors, are not only frequent but are also increasingly costly. The average cost of a data breach involving a vendor is now close to $2.70 million (AUD).
Notable Cyber Attacks Involving Third-Party Vendors
Recently there has been an increase in cyber-attacks and in particular the third-party vendor space. Notably the most recent high-profile example being SolarWinds. SolarWinds who provide software to help business manage their networks, systems and infrastructure were subjected to a large-scale cyber-attack which impacted major companies like Microsoft, cicso, Intel and government agencies. Hackers managed to circumvent SolarWinds systems and add malicious code into the companies Orion software which has around 33000 customers. Customers were impacted when SolarWinds unknowingly sent out software updates which included the malicious code, giving the hackers a backdoor to customer systems allowing the hackers to install malware and spy on companies and governmental agencies. The hack went undetected for months. Third party risk management (TPRM) must have a policy and a clear definition of the risk appetite within the third-party management space. Also, a definition of “third party” i.e., “business arrangement with another entity”, business requirements and frequency of assessments defined by the criticality. It is crucial to embed the TPRM process into the procurement and legal tendering processes within the company / organisation so the business can make risk-based decisions before entering into an agreement with a third party. It is also an opportunity to incorporate legally binding requirements into the contract based upon the results of any third-party risk assessment.The Need for Third-Party Risk Management
When companies outsource their processes or services, they expose themselves to a wide range of risks, including data risk, business disruption, legal liability, and compliance risk. Therefore, it is crucial to build beneficial, operationally effective relationships with third-party suppliers and monitor them frequently. This is where third-party risk management (TPRM) comes in.
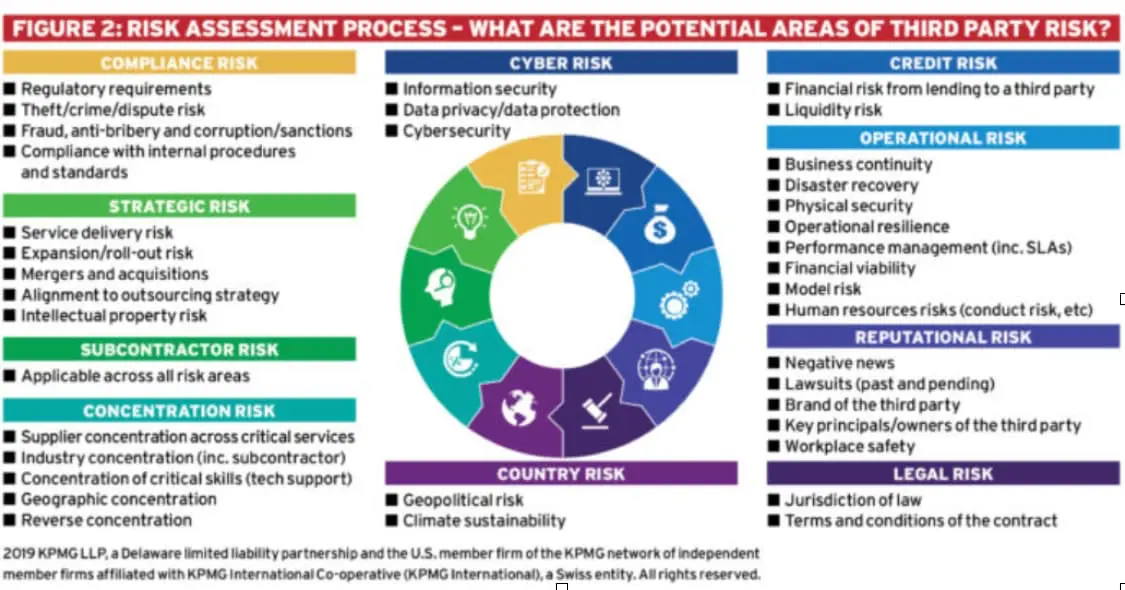 Third-party risk management (TPRM) can be divided into four key stages:
Third-party risk management (TPRM) can be divided into four key stages:
Summary.
Third-Party Risk Management (TPRM) is a structured approach to identify, assess, and mitigate risks associated with third-party vendors or suppliers. This process is crucial in today's interconnected business environment where companies often rely on external entities for various services and operations.
By following these stages, a company can ensure a comprehensive approach to third-party risk management, reducing the potential for unforeseen problems and enhancing overall security.